Imaging Steganography and Alternate Data Streams: The New Frontiers of File-Based Threats
By: Karrie Westmoreland
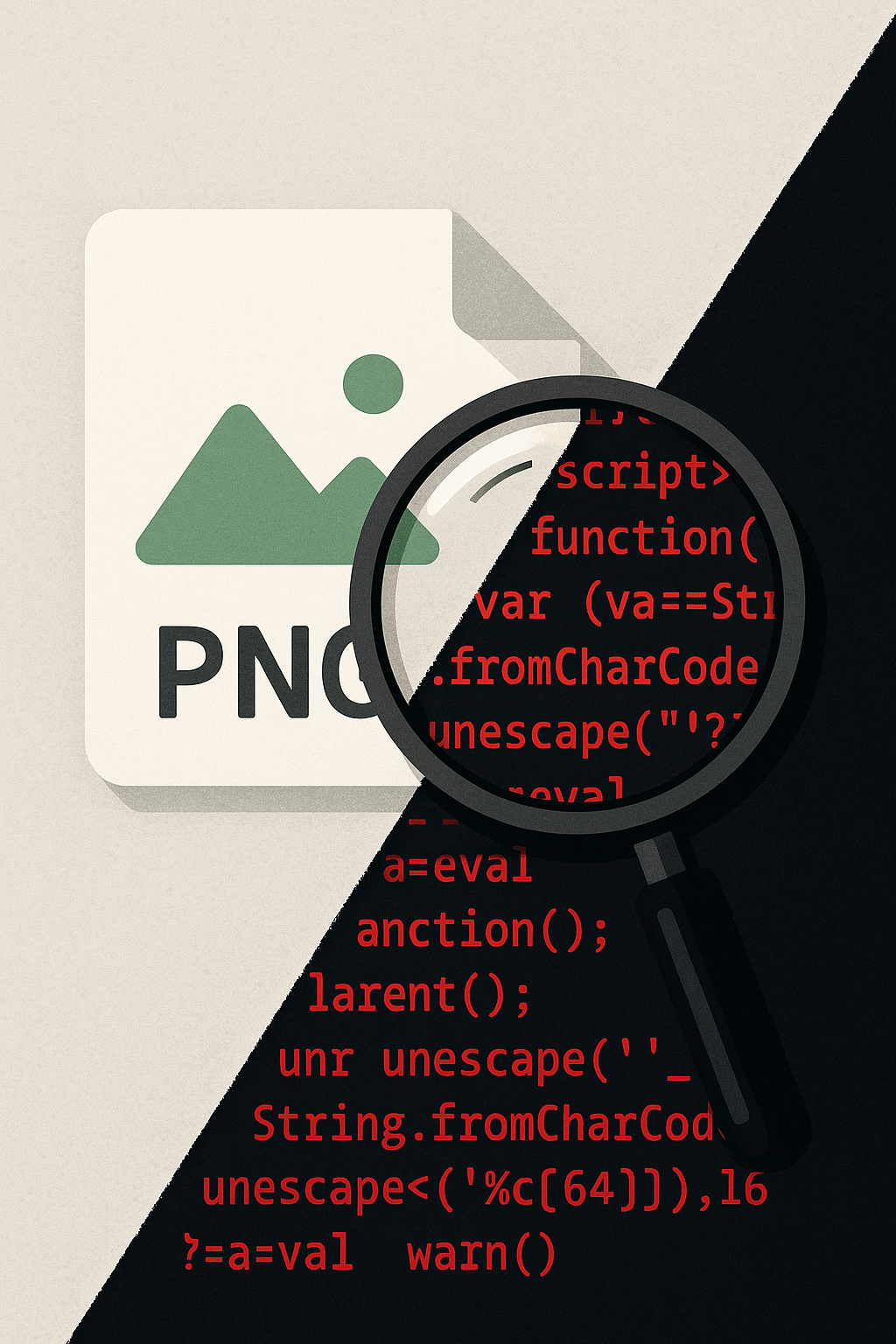








In today’s high-stakes digital landscape, partnering with the right cybersecurity provider can make or break your business. While large firms offer benefits such as scale and automation, many organizations are turning to boutique cybersecurity consulting firms for tailored, highly-individualized services that adapt to their specific needs.
